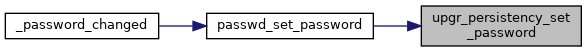#include <stdbool.h>Go to the source code of this file.
Functions | |
| void | upgr_persistency_init (void) |
| void | upgr_persistency_cleanup (void) |
| void | upgr_persistency_set_password (const char *const ani_path, const char *const password, bool hex) |
| bool | upgr_persistency_get_password (const char *const ani_path, char *const password, bool *hex) |
Detailed Description
Functionality related to saving and querying the upgrade persistent settings.
Definition in file upgrade_persistency.h.
Function Documentation
◆ upgr_persistency_cleanup()
| void upgr_persistency_cleanup | ( | void | ) |
Clean up the part responsible for the upgrade persistent settings.
The plugin must call this function once when stopping.
Definition at line 152 of file upgrade_persistency.c.

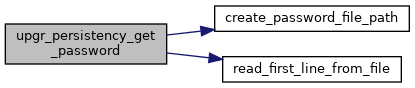
◆ upgr_persistency_get_password()
| bool upgr_persistency_get_password | ( | const char *const | ani_path, |
| char *const | password, | ||
| bool * | hex | ||
| ) |
Get the saved password for a certain ANI instance.
- Parameters
-
[in] ani_path path to ANI instance, e.g. "XPON.ONU.1.ANI.1" [in,out] password the function writes the saved password to this parameter if a saved password for the ANI exists. If no saved password exists, the function does not write to this parameter. The caller must pass a buffer of size MAX_PASSWORD_LEN_PLUS_ONE to ensure this function has enough space to write a password. [in,out] hex the function sets this parameter to true if the password it writes to password is in hexadecimal format.
If no saved password exists for the ANI, the function does not update password or hex, and returns true.
- Returns
- true on success, else false
Definition at line 242 of file upgrade_persistency.c.

◆ upgr_persistency_init()
| void upgr_persistency_init | ( | void | ) |
Initialize the part responsible for the upgrade persistent settings.
The plugin must call this function once at startup after it has called persistency_init(): if this function can not use the folder for upgrade persistent files, it uses the folder for reboot persistent files created by persistency_init().
Definition at line 112 of file upgrade_persistency.c.


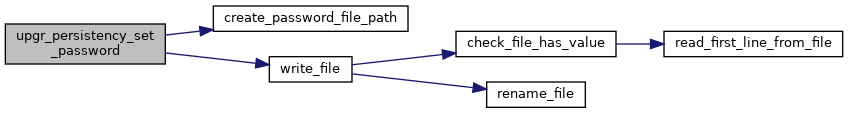
◆ upgr_persistency_set_password()
| void upgr_persistency_set_password | ( | const char *const | ani_path, |
| const char *const | password, | ||
| bool | hex | ||
| ) |
Save the password of a certain ANI instance.
- Parameters
-
[in] ani_path path to ANI instance, e.g. "XPON.ONU.1.ANI.1" [in] password new value for the parameter Password of the ANI referred to by ani_path [in] hex if true password is in hexadecimal format; if false, password is in ASCII format. The function only uses this parameter if password is not empty.
If password is empty, the function removes any files storing the password for the ANI instance.
Definition at line 185 of file upgrade_persistency.c.